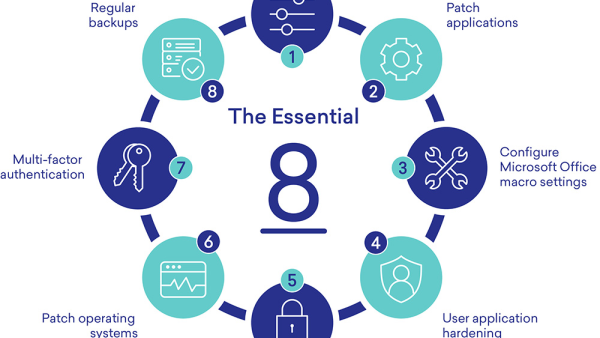
An Overview of the Essential Eight
News came out in 2021 about the Australian Government mandating the essential 8 Cyber Security controls for all non-corporate Commonwealth entities. This is scheduled to be put into practice starting June 2022 with a compliance audit every 5-years.