FTP (File Transfer Protocol) is simply FTP over SSL/TLS. Remember, SSL/TLS is protocol agnostic, and any communication protocol can be wrapped in a secure channel. FTP is simply a formalization of certain rules of engagement that clients and servers use to transfer files. SFTP on the other hand is part of the SSH protocol, which largely replaced Telnet and the earlier Rlogin as the preferred means to obtain a shell remotely against a *nix system. As of Server 2019, Microsoft includes a build of OpenSSH compatible with its Windows Operating system. While a little rough around the edges, it is a phenomenal choice for file transfer. Still, if you are working with older server Operating Systems, or have specific client-side requires for using FTPS (or if you are trying to support both protocol for maximum compatibility), read on.
Before we delve into securing FTP, it’s worth noting that FTP is capable of two main modes: Active and Passive. In Active mode, the client chooses a port within a predefined range (usually tens of thousands of ports!) and listens for incoming data connections. Both active and passive mode rely on two separate channels of communication: the data channel, and the control channel. By default, Active mode FTP uses port 20 for its data channel and port 21 for its communication channel. Passive mode FTP on the other hand uses a random ephemeral port for its data channel, and the flow of data is reversed: It is the server where data flows to, and many unique ports must be open on the server per client connection.
Either mode is a network administrators nightmare, (hence the popularity of SFTP). The NAT in people’s homes often thwarts active FTP mode in the modern day. Passive mode on the other hand requires having up to tens of thousands of ports open to the internet. Truly, using FTP or FTPS puts us between a rock and a hard place. Regardless, it is reasonably secure to host an FTPS server if proper controls are in place such as not joining the server to your domain and keeping it within a DMZ.
FTPS can leverage SSL/TLS in two ways. Using Implicit SSL/TLS, clients send their initial request to port 990, and the client begins with a TLS ClientHello. Very brusque if you ask me! In Explicit SSL/TLS, the FTPS client starts the communication as a regular FTP communication, but sends the special extended command “AUTH” to elevate to a connection which leverages SSL/TLS. If you are familiar with email security, this is roughly analogous to STARTTLS. Complicating things even further, FTPS (either explicit or implicit) can also be either Active or Passive. Is your head spinning yet?
Setup up FTPS in IIS
FTPS exists as an optional component of the IIS Web Server. This can either be enabled via server manager, or via:
shell
Install-WindowsFeature Web-FTP-Server -IncludeAllSubFeature Install-WindowsFeature Web-Server -IncludeAllSubFeature IncludeManagementTools
After installation, when you go to create a site in IIS, a new option will appear: Add FTP Site
It will need a physical path. I like to create a folder at the root of C:\ and create subfolders for each FTP user.
Select Next.
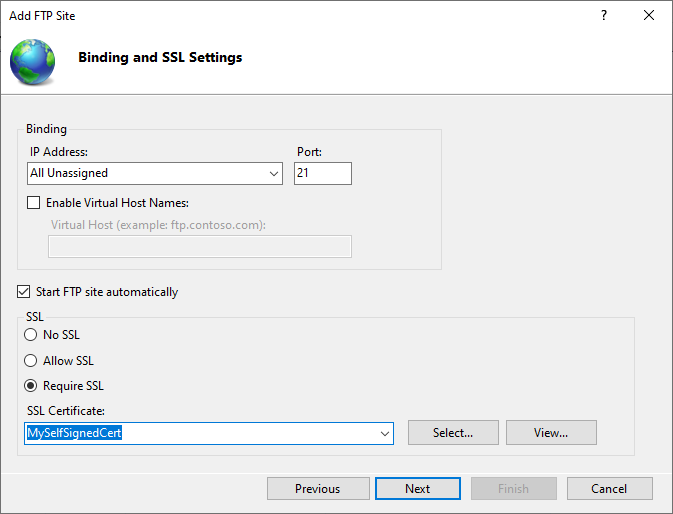
I am using a self-signed cert for the purposes of demonstration, but for the connection to be trusted by your user’s FTP client, you will need a publicly signed ssl certificate (the same as you would use for an HTTPS connection). This can be procured right from the main ssltrust.com.au site!
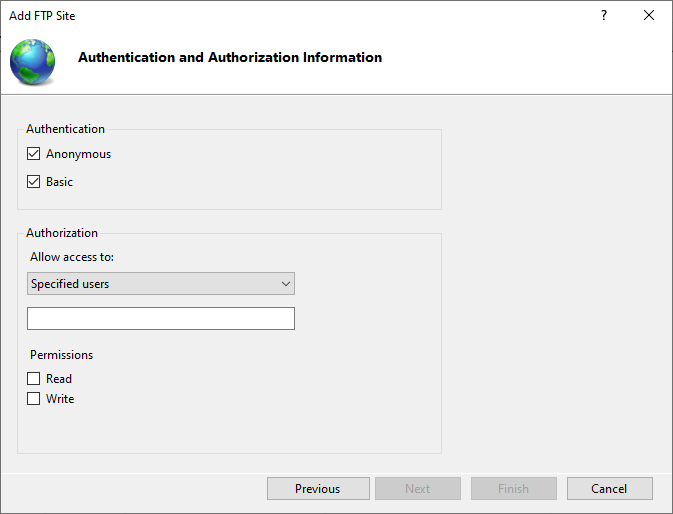
Permissions can be scoped granularly to the FTP site. Anonymous access allows anyone to read or write content to this folder. Be very careful with this permission level! Basic Authentication allows local accounts to be setup in the local user manager on the machine. Notably, there is no concept of Windows Authentication for FTP.
Selecting the site allows us to change FTP related settings.
In order to setup support for Passive mode, you must configure your external NAT IP under FTP Firewall Support:
You will need an FTP Authorization rule in order for users to be allowed to connect without receiving an “Access Denied” message.
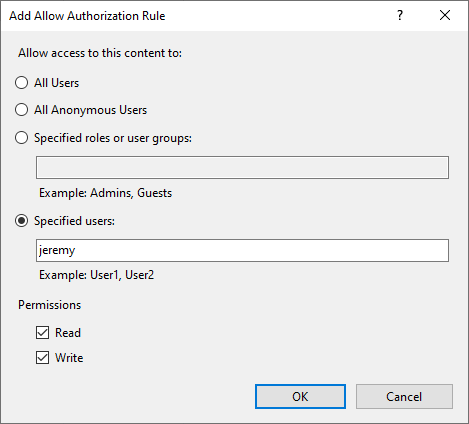
This will allow the local windows user “Jeremy” access to read and write to the site.
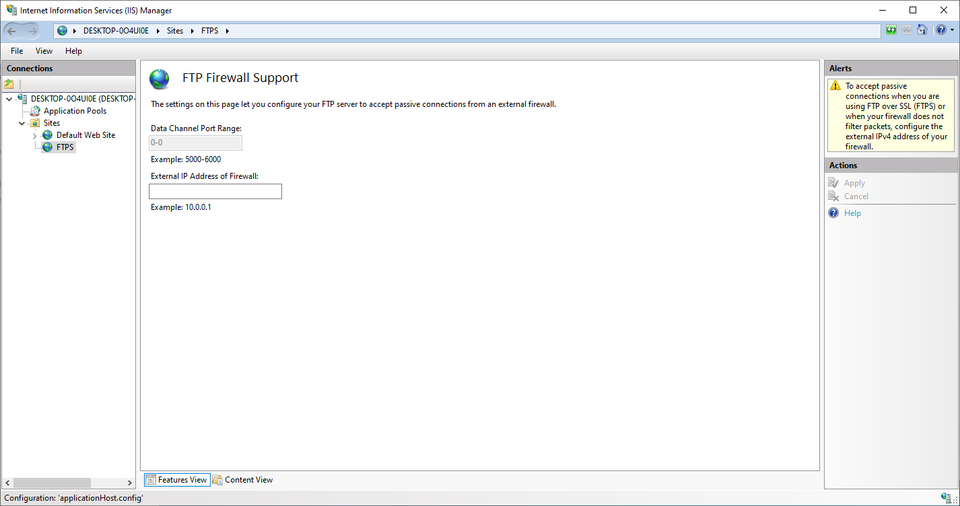
Note that you can only change the Data Channel Port range if you navigate to this configuration menu at the server level instead of the site level. If 0-0 is used, you must forward all ports (or make your server available directly on the public internet).
One popular FTP client is WinSCP, which also supports the more commonly used SSH protocol.
The following yields a successful login:
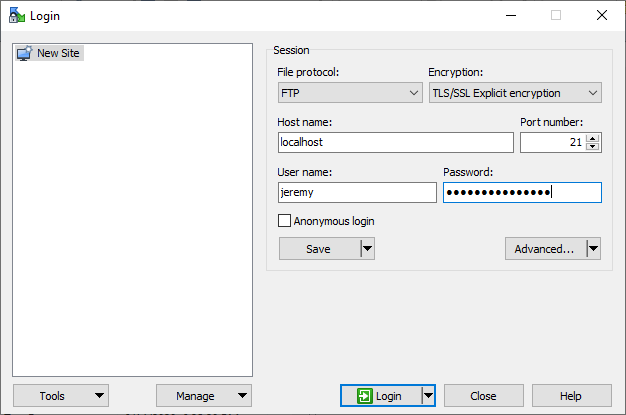
While mostly supplanted by SFTP, in a pinch, it is useful to have the know-how to setup an FTPS server on IIS. I frequently use this technique in order to move logs from network equipment or move upgrade images to networking equipment. (Technically speaking, TFTP is a different protocol that consists of a subset of what FTP can do, but IIS’s FTP server implementation can also effectively serve TFTP clients). For internal transfer of data, it is often superior to SMB, which is unencrypted by default. Ultimately, though dated, FTP will likely continue to be a supported option in many environments for years to come.
Discussions and Comments
Click here to view and join in on any discussions and comments on this article.

